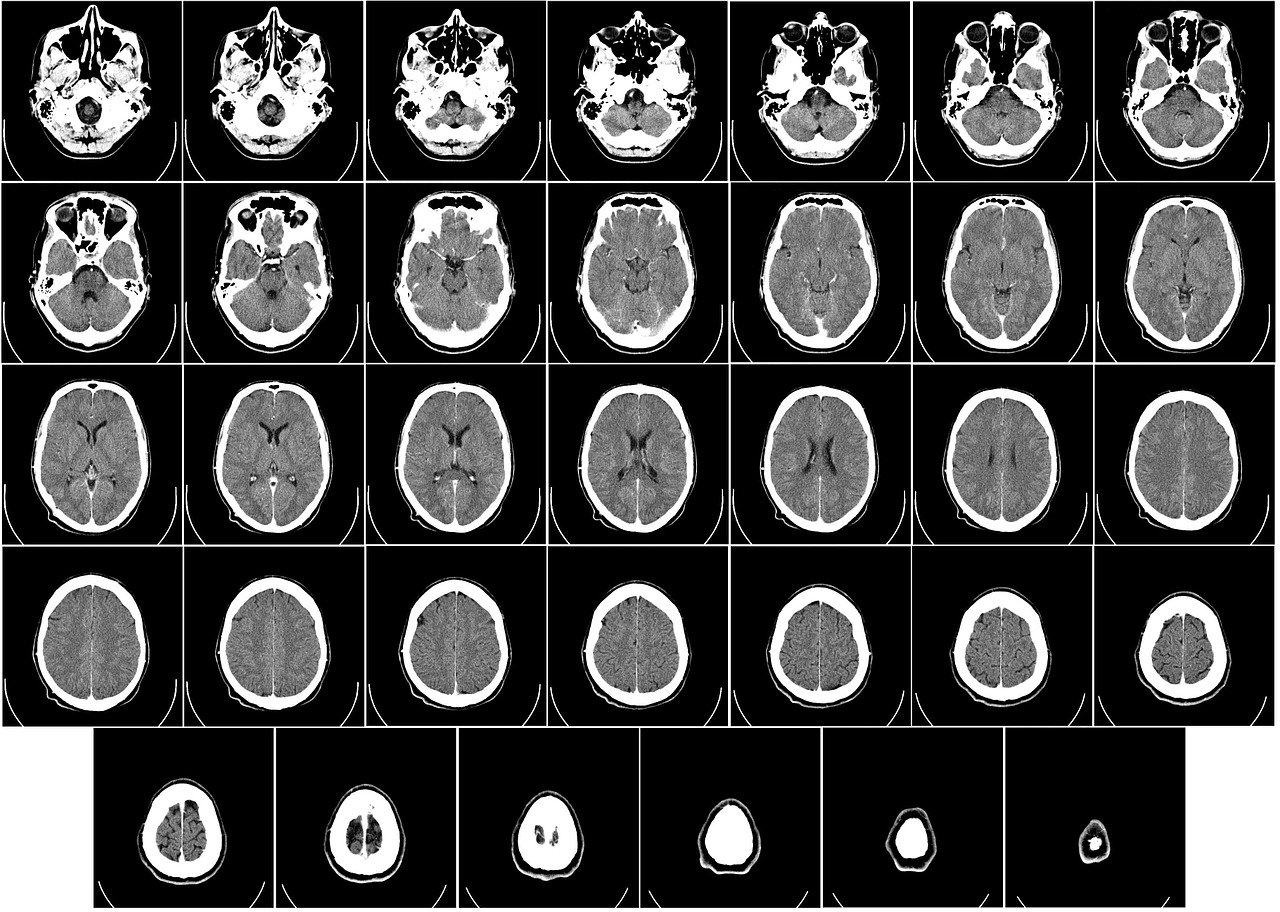
Ultrasound is used in many different fields. Ultrasonic devices are used to detect objects and measure distances. Ultrasound imaging or sonography is most often used in medicine. In the non-destructive testing of products and structures, ultrasound is used to detect invisible flaws. Industrially, ultrasound is used for cleaning, mixing, and accelerating chemical processes.
Diagnostic ultrasound is a non-invasive diagnostic technique used to image inside the body. Ultrasound probes, called transducers, produce sound waves that have frequencies above the threshold of human hearing (above 20KHz), but most transducers in current use operate at much higher frequencies (in the megahertz (MHz) range). Most diagnostic ultrasound probes are placed on the skin. However, to optimize image quality, probes may be placed inside the body via the gastrointestinal tract, vagina, or blood vessels. In addition, ultrasound is sometimes used during surgery by placing a sterile probe into the area being operated on.
- Diagnostic ultrasound can be further sub-divided into anatomical and functional ultrasound.
- Anatomical ultrasound produces images of internal organs or other structures.
- Functional ultrasound combines information such as the movement and velocity of tissue or blood, softness or hardness of tissue, and other physical characteristics, with anatomical images to create “information maps.”
These maps help doctors visualize changes/differences in function within a structure or organ.
Here more information and background:
https://www.nibib.nih.gov/science-education/science-topics/ultrasound
Examples for ultrasound examination in the Femtech area:
Obstetric ultrasonography, or prenatal ultrasound, is the use of medical ultrasonography in pregnancy, in which sound waves are used to create real-time visual images of the developing embryo or fetus in the uterus (womb). The procedure is a standard part of prenatal care in many countries, as it can provide a variety of information about the health of the mother, the timing and progress of the pregnancy, and the health and development of the embryo or fetus.
Breast ultrasound is a medical imaging technique that uses medical ultrasonography to perform imaging of the breast. It can be performed for either diagnostic or screening purposes[1] and can be used with or without a mammogram. In particular, breast ultrasound may be useful for younger women who have denser fibrous breast tissue that may make mammograms more challenging to interpret.
Vaginal ultrasonography is a medical ultrasonography that applies an ultrasound transducer (or “probe”) in the vagina to visualize organs within the pelvic cavity. It is also called transvaginal ultrasonography because the ultrasound waves go across the vaginal wall to study tissues beyond it.
Ovarian cysts are usually diagnosed by ultrasound, CT scan, or MRI, and correlated with clinical presentation and endocrinologic tests as appropriate.
Pelvic congestion syndrome, also known as pelvic vein incompetence, is a long-term condition believed to be due to enlarged veins in the lower abdomen. The condition may cause chronic pain, such as a constant dull ache, which can be worsened by standing or sex. Pain in the legs or lower back may also occur.
Current advances of Ultrasound in the Femtech area:
GE HealthCare designed the ultrasound systems to integrate AI, advanced tools and an ergonomic design. They speed exam time for clinicians while delivering a clearer picture of various conditions impacting women’s health. The latest systems combine high-performance hardware with flexible, scalable software to help increase confidence in diagnostic and treatment decisions.
AI-enabled ultrasound technologies support clear, quick and confident diagnoses. This latest launch helps to address patient demand and reduce staffing burdens by giving clinicians these tools.
New, improved and enhanced Features are:
- Features include voice commands and the SonoLyst suite of AI tools. SonoLyst tools identify fetal anatomy and annotate and measure where applicable. This can reduce the time to complete second trimester exams.
- simplifies assessments of the pelvic floor and speeds up exams as well. It automates plane alignment and measurements for high keystroke reduction.
- They integrated the technology with its Vscan Air CL wireless dual probe. With a flexible, wireless workflow, users gain a wider range of motion.
- FetalHS simplifies and speeds fetal heart assessments with step-by-step, AI-driven guidance for identifying normal fetal heart anatomy.
Conclusions and Opinions
- With proven time-saving AI-driven applications, and advanced automation features that simplify exams, the technology can help enhance ease of use and provide clearer images, helping clinicians power through demanding workflows faster while delivering greater consistency and accuracy, ultimately helping deliver better health outcomes for women.
- The new Voluson Signature series features innovative tools clinicians can rely on, and the automated functions help reduce work stress and improve workflows
- A new era of ultrasound scanning.
Here the link to the article of +MASS DEVICE:
https://www.massdevice.com/ge-healthcare-launches-ai-ultrasound-womens-health/